Some malefactors just don’t know when to stop. First, we saw malware masked as files about coronavirus, and now they’re sending phishing e-mails that exploit the very same epidemic.
Phishing with the coronavirus for e-mail credentials
The letters appear to come from the Centers for Disease Control and Prevention, which is a real organization in the United States, and they do recommend some actions regarding the coronavirus. The e-mails also come from a convincing domain, cdc-gov.org, whereas the CDC’s real domain is cdc.gov. A user not paying careful attention isn’t likely to notice the difference.
The letters claim that the CDC has “established a management system to coordinate a domestic and international public health response” and urge recipients to open a page that allegedly contains information about new cases of infection around their city. The link appears to point to the legitimate CDC website: cdc.gov.
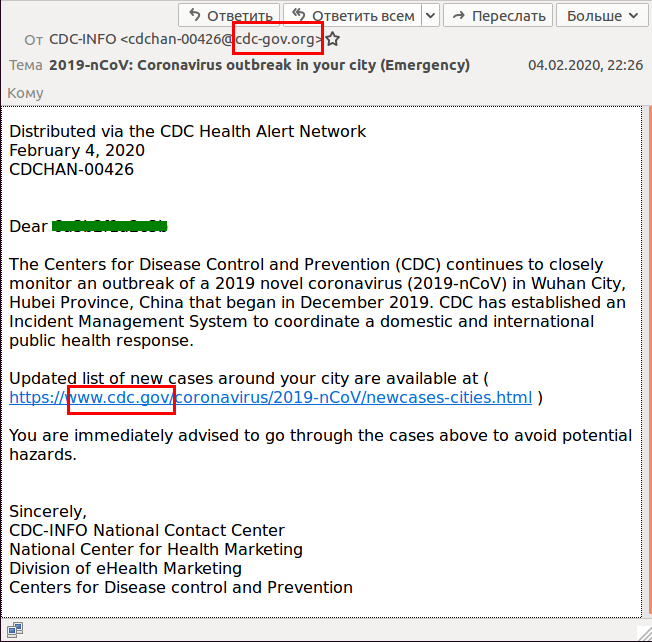
Coronavirus phishing e-mails appear to come from the Centers for Disease Control and Prevention (CDC)
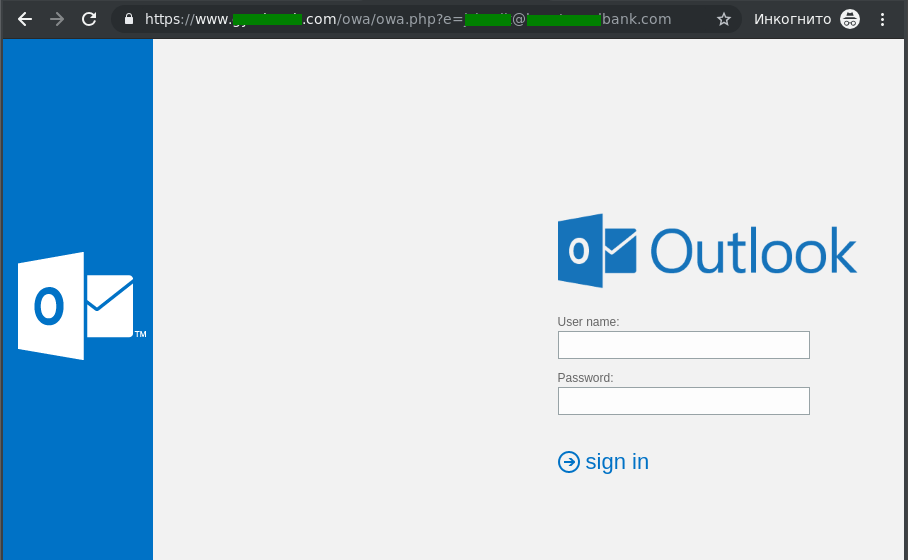
The website looks similar to Microsoft Outlook’s interface — and requests an e-mail login and password. Of course, the website has nothing to do with Outlook; it’s just a page crooks built to steal e-mail credentials. It won’t log you in anywhere, but it will forward your login and password to the criminals, who will later use them to access your e-mail account and look for anything worth stealing in there.
What’s the catch in coronavirus phishing?
To avoid getting hooked, pay attention to details. Three things in this particular scheme should raise red flags:
- The e-mail address of the sender. If it ends with cdc-gov.org instead of cdc.gov, the e-mail is phishing.
- The actual URL of the link. If you hover over the link without clicking on it, you’ll see that the real address it leads to is different than the link description. It won’t really bring you to cdc.gov.
- The design of the phishing page. The official Microsoft Outlook website actually looks completely different. Of course, no website other than Microsoft’s should ask for your Outlook credentials. If you see such a request, know that it’s phishing and ignore it.
If you pay attention, you will certainly notice at least one of the problems we list above, but even one is enough to tell you: This is phishing, so don’t click any links, download any attachments, or enter any credentials.
The coronavirus as a topic is heating up among malefactors of various kinds, so expect to see other malicious campaigns using the deadly virus as bait. Recently we’ve seen spam campaigns selling masks, which some perceive as the first line of defense against the virus.
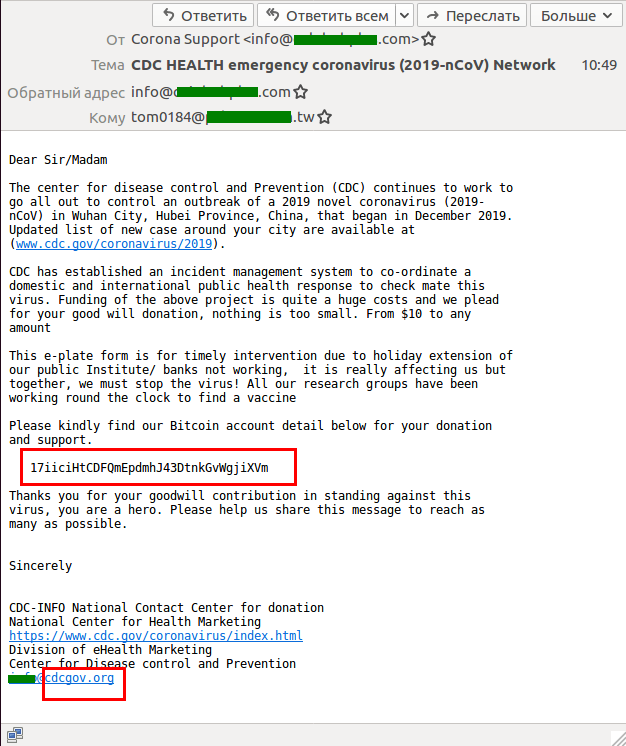
Another example we encountered recently was another phishing e-mail that also appeared to be sent from the CDC, this time from a different — but still fake — address: cdcgov.org.
This e-mail urged recipients to donate Bitcoin to fund coronavirus vaccine research. Of course, the real CDC does not accept Bitcoin, and it is not asking for donations. And we’re sure to see more scams exploiting coronavirus fears.
How to protect yourself from phishing
- Attentiveness and knowledge are your two best tools. Look carefully to spot wrong addresses, misspelled domains, URLs with misleading labels, and other signs. To learn more about typical phishing methods and techniques, read our ten tips for avoiding phishing and other posts about phishing on Kaspersky Daily.
- Use a reliable security solution, such as Kaspersky Security Cloud, that automatically detects phishing websites and blocks access to them.
 phishing
phishing

 Tips
Tips